9 Ways You’re Losing Your Privacy
We live in an age where we’re exposed to an incomprehensible amount of information and communication. We have access to the internet, social media, email, online file storage, online shopping, and much more. However, all of this information is managed somewhere, even if you think it isn’t.
Google accounts, Apple accounts, social media accounts, Amazon accounts, bank accounts, and much more can be linked up, synced up, and hooked up to make sure that you have access to whatever you want whenever you want. But is all of this interconnected information really a good thing?
Here are 9 ways that your privacy is being invaded that you may not know about.
1. Amazon Echo
Amazon’s Echo and EchoDot are new staples of home electronics, but they have not come without privacy problems. The Echo consistently listens to any conversation in the room it is located in and waits for you to say the “wake word,” which is either “Echo,” “Alexa,” or Computer, depending on the settings. The Echo then transcribes and sends all conversation to the Amazon Cloud, where it can be viewed later on the computer or phone with your Amazon account.
However, many skeptics have pointed out that since the Echo is always listening, what’s stopping the Echo from transcribing any conversation you have with or without the wake word? And what does Amazon do with all of this stored information? Who else sees it?
2. Google Maps on iOS
Google Maps on iOS has recently released a new feature called “My Timeline.” The feature tracks where, when, and for how long you went somewhere, making a note of your route and mode of travel.
Even if this feature could be useful, it was installed and enabled without the user’s permission. Many users were completely unaware that this feature even existed, let alone how to disable it. Why even use it in the first place? Google seems to be recording more information than necessary here.
3. Laptop Cameras
This belief is so popular that it has become a meme on its own. The debate that the government spies on people through their laptop cameras has been around since the Digital Age existed. It doesn’t help when security officials and technology giants cover up their front facing cameras with tape (we’re looking at you, Mark Zuckerberg).
There’s a whole business for camera covers. But it’s no surprise that hackers can very easily post virus and malware on the internet to trick people into downloading, giving them free access to your laptop camera. No one knows what they’ll do with the footage afterwards. Don’t want Big Brother to see you watching Netflix and eating a whole pint of ice cream? Cover the camera up.
4. Telephone Scams
When you receive an unknown call and an anonymous voice keeps asking, “Can you hear me,” don’t respond. The growing concern is that your answer is being recorded and then being used to approve fraudulent charges purchased with your information. Who knew a simple yes could lead to so many problems, including identity theft?
5. Facebook Ads
It’s no coincidence that when you Google one item, ads for it appear on the sidebar of your Facebook page within minutes. Really, it isn’t.
Facebook makes use of third-party cookie tracking to log your browser history and use it to strategically place relevant ads on your page, hoping to collect more money from your clicks (seriously, I had two ridiculously specific ads for my favorite Broadway show and gluten-free cookies on one page while researching this).
Facebook claims this “marketing strategy” is just a more effective way to advertise. But does Facebook really need to know this much about me? And why must it keep track of my entire browser history to show me ads for flourless cookies?
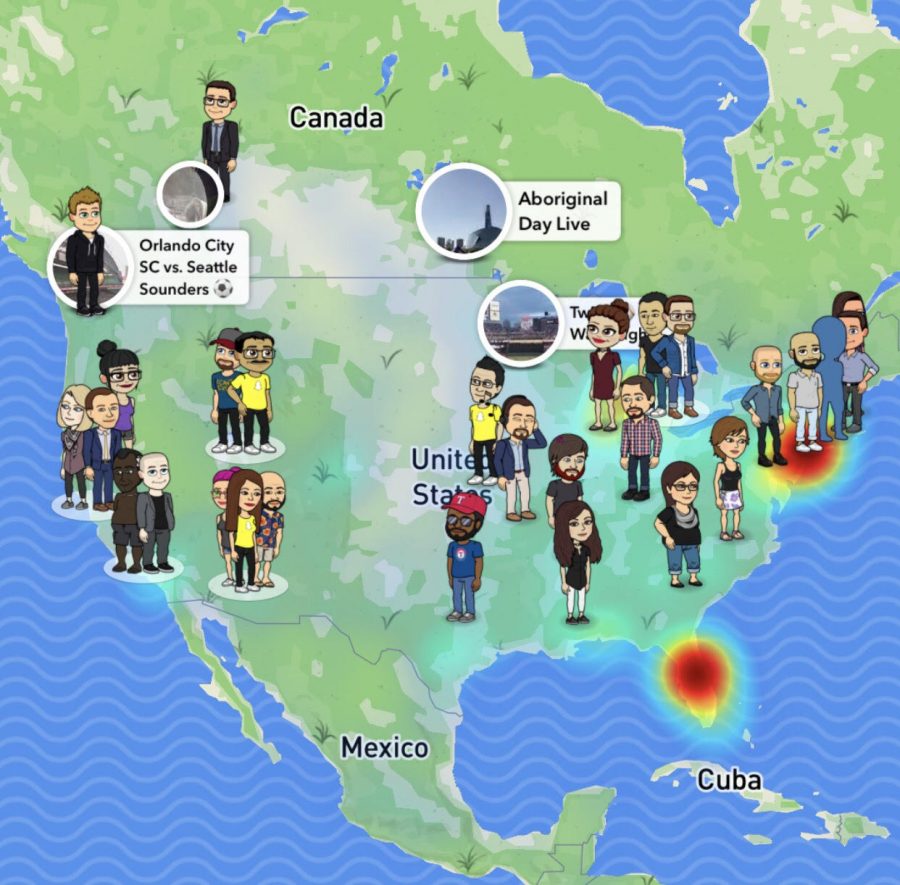
6. Snapchat’s Snap Map
The Snap Map was supposed to show the location of your friends’ Snap Stories when they were posted, but most users didn’t understand that without careful setup the Map broadcasted your exact location whenever the user opened the app on their phone. Not creepy at all.
7. Virus Fixers
If you receive a popup that you have a virus, chances are you don’t. Somebody just wants you to think that you do.
If you ever are informed that you need to pay to have your virus removed, do not under any circumstances give away your credit card information.
Hackers will try to convince you that you need service on your computer to fix it. People have been financially ruined over this simple mistake. The “virus fixers” will steal your information, hack your credit card, and you may never figure out that they did.
8. iTunes Receipts
Always be wary of iTunes emails from Apple, especially if they ask you to sign in or enter your password. Unfamiliar purchases ($90 on Pandora, $65 on Spotify, etc.) are often warning signs. Hackers can install malware on your device just by your opening the email, let alone following your keystrokes and stealing your username and password. By hacking into your Apple ID, they have almost unlimited access to your Apple Pay, Apple account, device settings, and much more.
9. Repeal of the FCC
When Congress repealed the Federal Communications Commission’s (FCC) privacy regulations for Internet Service Providers (ISPs) last year, it allowed Big Brother companies like RCN and ServiceElectric to track your internet usage, browser history, and internet downloads, and then sell that information to third party companies to give them fodder to assault you with advertisements. Sure, those ads may be harmless, but really? Why do these huge information giants get to sell our information to random companies for their sole benefit?











Dorothy Glew • Mar 5, 2018 at 11:23 am
I would like to see the Federal Communications Commission’s (FCC) privacy regulations for Internet Service Providers (ISPs) restored. I want privacy!!!